Exploitation of Triadic Closure on Social Media
In social networks, triadic closure can be used to forecast certain relationships. For instance, if two people have ties with a third person, there is an increased probability of the two people becoming friends. The triadic closure principle also extends to social networking sites such as Facebook and LinkedIn. Although triadic closure encourages the formation of new relationships, studies have shown that it is also a valuable tool for online users with malevolent motives.
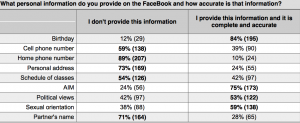
As concerns about susceptibilities in Facebook and other social networking sites grew, the University of British Columbia created 100 fake profiles and sent 5,000 friend requests to examine users’ willingness to accept friend requests from strangers. According to the results, 19% (595 users) accepted the first round of requests. The fake users then sent friend requests to the friends of the 19%, and 59% of those friends accepted the requests. These data show that people are three times more likely to accept a stranger’s friend request if they share mutual friends with him or her. For instance, is node A has strong ties to nodes B and C, nodes B and C will share either a strong or weak tie. It is less likely for nodes B and C to share a bond if they are not connected to node A. This highlights the vulnerabilities the triadic closure principle can pose on social media platforms. By turning a blind eye, people unintentionally expose a wealth of personal information (email addresses, phone numbers, children’s names, dates of birth, current locations, etc) that become the basis for identity theft attacks and fraud exploits. According to the table below, when users provide information, it is likely to be complete and accurate.
Although securities incidents on social media have become more widespread, users can decrease their vulnerabilities by adding new contacts online with extreme caution.
Sources:
http://people.cs.pitt.edu/~chang/265/proj10/zim/imaginedcom.pdf
http://www.ittoday.info/Excerpts/Before_You_Go.pdf
