NSA Embodying the Strong Triadic Closure Principle to Locate Terrorist Groups
https://www.forbes.com/sites/gregsatell/2013/06/07/how-the-nsa-uses-all-those-verizon-phone-records/#35490c602d71
This article discusses how companies such as NSA are using phone records from Verizon to track down terrorists. Initially, this concept seems very unfocused and unrealistic, however this article incorporates The Strong Triadic Closure which states that if person A has a strong connection with person B and person B has a strong connection with person C, then there is a strong likelihood that there exists some connection between person A and person C which may be either strong or weak. In essence, Strong Triadic Closures help build large communication networks. Sociologist Mark Grannovetter “argued that we get our information mostly from weak ties”. That means that NSA is trying to figure out the communication between A and C to find out more about the activities, A B and C are involved in collectively. In this case, the NSA is also assuming that if were discussing about three members A, B and C in the Triadic closure, and that if AB and AC were strong ties, then there must be some type of relationship between BC which will be a weak tie. The NSA is under the assumption that the weakest links will provide the most information because they are the most unsuspecting. The NSA is out to look for many “BC” like weak ties in triangles that collectively form a network, because knowledge about how these weak ties interact could be very useful for understanding terrorists, their plans, future attacks, etc.
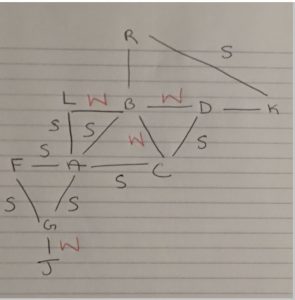
Extending the network/ABC triangle mentioned above, let’s just say that there is another person L and that the AL tie is a strong tie. Since we know that AB is a strong tie, there is an increased chance that LB has a relationship which could be strong or weak. Let’s say that the phone records show this interaction between L and B to be weak. Let’s also introduce person G who has strong tie with new person F and a strong tie with A. There is an increased likelihood that person A and F will have some sort of relationship which could either be strong or weak but which we’ll assume to be strong in this case. So there are many mutual connections within this expanded network group which can be useful in figuring out various terrorist groups and their members. In Triadic closure, the “the third latch” doesn’t necessarily have to be a strong tie, it can be a weak tie if there isn’t a lot of communication among those two people. It’s more difficult to find these weak ties though because there isn’t that much data of their interactions.
The article also discusses assumptions about how the NSA needs to make sure that these weak ties are not due to friendly neighbors or delivery men because that would result in inaccurate information. If the NSA wants to find people who interact with terrorists but don’t have any affiliation with them, they can look for random connections in which person Q is connected to person P and Person T but person Q doesn’t have mutual friends with P and T. For example, in the drawn example below, person R is only connected to person B and person K and person R isn’t friends with any of B and K’s friends. This would indicate that all of them are not connected, and therefore the “random person” R who doesn’t have mutual friends with R and K would be the likely one who isn’t a terrorist.
Additionally, if they are on the look for “weak ties”, and people connected with terrorists, NASA can go beyond the Triadic Closure and focus on local bridges which are also weak ties. In the example below, J forms a local bridge with G since it’s only connected to one member in the network. Therefore, J would be credited with giving novel information to G which nobody else in the network will know about. I believe the NSA would really value trying to find these local bridges in terrorist networks as their next plan of action.