Determining the Anonymity of Bitcoin using Networks
The concept of remaining truly anonymous on the Internet is a very elusive idea. One area where this has been of particular interest recently is in the use of Bitcoin in creating anonymous digital transactions. Bitcoin was created around 2009 by researcher Satoshi Nakamoto as an attempt to exploit the power of the Internet to create a decentralized and untraceable form of online currency. The idea is that, instead of storing actual objects or “coins” in your account, you can instead store a history of all transactions that you have made. In fact, every transaction that anyone has ever made is publically available in something called the block chain. However, the only information that could potentially identify those participating in these transactions are their addresses—public keys that most users change after every transaction. It is believed that the more secret, private key that could potentially identify an individual involved in these transactions remain secure and untraceable.
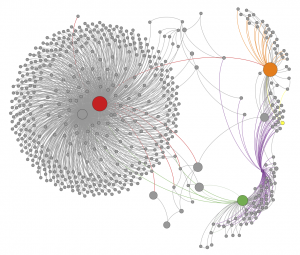
Two researchers from University College Dublin, however, have speculated that observing the public transaction records as a networks could potentially be used to break the anonymity of Bitcoin transactions. They show this by considering two case studies, the first of which involves an attempt to identify a thief accused of stealing more than 25,000 Bitcoins (According to Google’s estimated Bitcoin price of $463.88 each, this equates to over $10 million today). This is done by considering the transaction history as a graph, with each node being a public key and each directed edge representing a transaction between two public addresses. This can be seen in the following image of a portion of the graph, where the red node represents the suspected thief, the green node represents the victim, and the orange node represents a hacker group that was originally suspected in the robbery:
By observing patterns in the structure of the network shown and its surroundings, the researchers were able to connect different public keys together that were very likely to belong to the same users (for instance, an address that stole a single Bitcoin from the victim directly before the massive robbery likely also belonged to the thief). In this way, they could learn more about the nature of supposedly anonymous transactions between the different parties involved in the robbery.
In another case study, the researchers consider the issue of determining the identities of those involved in “anonymous” donations to Wikileaks, demonstrating a potentially more legitimate use for an anonymous currency. It is interesting to note that the breach in anonymity, in both of these cases, comes not so much from exploiting a technical flaw in the Bitcoin system, but rather from simply noticing patterns in the network that correspond with typical human behavior. The researchers go on to reply in a comment on their article that while “it is possible to use Bitcoin in a way that is almost certainly anonymous,” users who expect this luxury as the default for using Bitcoin may find themselves in trouble. While the technology behind Bitcoin does indeed provide for technically anonymous transactions, the patterns of human behavior that networks reveal can still be used to reveal a person’s identity.
Main Article:
http://anonymity-in-bitcoin.blogspot.com/2011/07/bitcoin-is-not-anonymous.html
Bitcoin Information:
https://en.bitcoin.it/wiki