(Ab)using Triadic Closure
While traditional brute force hacking remains to be a large problem for users and computers alike, there is a growing problem with ever increasing users online: social engineering. According to the Oxford English Dictionary, social engineering is defined as “the use of deception in order to induce a person to divulge private information or esp. unwittingly provide unauthorized access to a computer system or network.” In a recent paper by Boshmaf et al., online social penetration as a method of social engineering was studied.
With the ubiquity of the Internet and the recent surge in social networking, it has never been easier to find people’s information online. In particular, users of Facebook, a popular social networking website, has been a frequent target for online information gathering. While privacy settings on Facebook have improved over the past several years, allowing its users to block information from strangers and only allowing access to approved friends, individuals have found a way to abuse the human aspect of social networking for malicious purposes.
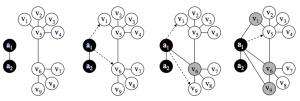
As we learned earlier in the course, triadic closure refers to a concept in networks theory, in which if node A has strong ties with nodes B and C, B and C will share a bond, weak or strong. While the theory does not hold for every network, it is strong tool for predicting networks, including social networks. In the aforementioned paper, Boshmaf et al. designed a strategy that abuses the triadic closure in order to attain personal information on Facebook. In order to access various personal information–including phone numbers, dates of birth, private e-mail addresses, and personal photos–only available to friends, the students at University of British Columbia designed a program that will friend random individuals, analyze the available network of friends, then determine the next victim using the triadic closure principle (see Figure 1).
Figure 1. Illustration of how the triadic closure was applied in the experiment.
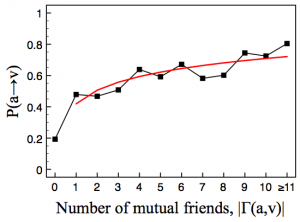
Using these tools, out of 8,954 users they tested, 3,055 users (54.6%) accepted the malicious friend requests. On the experiment, which ran for six weeks, they found increasing rates of success rates as the number of mutual friends increased, from 20% with no mutual friends to close to 80% with 11 or more mutual friends, as illustrated on Figure 2. To satisfy triadic closure, strong ties are necessary. Considering that many of the initial friends may not be close friends, it is no surprise that there is improvement in the success rate with increasing mutual friends.
Figure 2. Success rate vs. number of mutual friends
While the concept of triadic closure is rather an intuitive one, it is very interesting to observe it being applied in the real world, as effectively as in this situation. With increasing fears regarding security in online social networking websites, more research on social networks theory should be done, in hopes of preventing efforts like the one in the experiment.
References
- Boshmaf, Yazan, Ildar Muslukhov, Konstantin Beznesov, and Matei Ripeanu. “On the Penetration of Online Social Networks: Exploiting the Social Structure.” University of British Columbia, 2011. Web. <http://lersse-dl.ece.ubc.ca/record/258/files/social_pen_TR.pdf>.
- “social engineering, n.”. OED Online. September 2011. Oxford University Press. 29 September 2011 <http://www.oed.com/view/Entry/272695?redirectedFrom=social%20engineering>.