Virtual Parasites: Browser Hijacking and Fraud in the Information Age
Today, we can seek pretty much whatever we want through a mouse click. The proliferation of the Internet has changed the way many of us acquire information. This has given rise to a plethora of search engines like Google that generate revenue partly by displaying advertisements in their search results, or by linking to them. However, this has also created a niche for hijackers and “malvertisers”, who employ similar methodologies, albeit in a more surreptitious and sinister manner.
What is hijacking?
Hijacking occurs when a third party member and/or organization forcibly (and illicitly) modifies the user’s browser and/or operating system (oftentimes without the latter’s knowledge and permission) in an attempt to obtain their personal information and/or generate revenue.
How does it work?
Think of it a parasite that mimics its host after infecting it.
Hijackers operate pretty much the same way Google does in generating revenue through advertising and collecting and distributing of user information, but with less transparent and more authoritarian means.
Sometimes clicking a link is all it takes for an infection to occur. Oftentimes such occurrences are surreptitious in nature such that a malicious program is installed without the user’s knowledge.
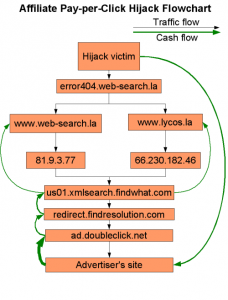
Unbeknownst to the victim, the “engine’s” primary intention is to force hits and generate ‘clicks’ to a particular site, thus increasing advertising revenue that will then be divided amongst all parties involved in the scheme.
Infection Vectors and Syndication
Sites that have a large authority, or a large number of sites linking to them, are hotspots, due to their high authority scores. Popular misconception is that commonly-visited sites are “legitimate” and therefore less “sketchy”, which means that they are not vulnerable to fraud. Google’s Page Rank algorithm usually assigns them a high score, which means they appear in the search results quite often because there are many sites that link to them. This implies that their credibility is high and thus, users have less incentive to monitor them with the same level of scrutiny that they do with less-known sites. As a consequence, they are led to erroneously conclude that all advertisements on the site are non-malicious. Bottom line: the more traffic a site has, the more vulnerable to hijacking it becomes. Once compromised, an infected site is likely to transmit the disease to the sites it links to, making them potential infection vectors.
A Few Known Cases
News and social media sites are prone to hijacking because they constantly have high traffic, or a consistently large population of users that frequent them. These sites have high hub and authority because they link to many pages and have many pages that link to them, making them the ideal hosts.
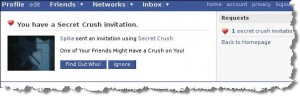
In 2008, Facebook was compromised through a fraudulent app known as “Secret Crush”. The app would generate an external link on the infected user’s wall page, under the guise that it was authored by the user himself. It was virulent in nature in that it infected all parties that clicked on the link. The malware exploited the fact that people were likely to trust their friends.
In September of the following year, the New York Times inadvertently hosted a malicious ad that disguised itself among a Vonage (a common sponsor) ad. Clicking it resulted in a pop-up window that purportedly informed the user that their computer was infected with viruses. Users were then led to install an “anti-virus” which was itself a virus.
Why should we care?
The Internet has become closely integrated within our lives and there are people who seek to exploit this to our detriment.
Basically it is in everyone’s (or most of society) interest that the Internet remains as free as we can make it. Malvertising, or hijacking gives people less incentive (and less reassurance) to use the web, which can hurt individuals and firms that depend on the web for their income by eroding the public’s confidence. Sometimes the damages are extremely costly to fix.
Lastly, malvertising threatens user privacy in the sense that their personal information is acquired (without their knowledge and permission) by an illicit third-party and can possibly be used against them in malicious ways via fraud and identity theft. News, social media, and email-hosting sites, which are commonly visited by the majority of Internet users, are ideal for hijackers due to their high traffic (thus, high hub and authority) and them being carriers of a plethora of personal information.
If we hope to combat hijacking, the least we can do is increase the public’s awareness of such frauds.
Link to Article/Paper:
http://www.looksmart.com/assets/Uploads/browserhijackingreport.pdf