ALERT: Facebook Security System – Is it Enough?
When a stranger adds you on facebook, do you accept the request or report it to the security system? Personally, I have been accepting such requests as long as users displayed profile photos (stupid me – I wasn’t thinking that they could put fake photos). So today, I decided to go through the list of these suspicious facebook friends. Many of them were actually ordinary human beings trying to interact with any facebook users. However, there were a couple of suspicious “friends” with only one display photo, without any user-user interactions whatsoever other than adding hundreds of users. Nowadays, one big issue with social networks is the security system. Can we trust the spread of our personal information throughout a network system? Is it secure to share information among friends on such a system?
The Facebook platform, which began as a modest social network to track classmates at Harvard University, has expanded into a ubiquitous Internet phenomenon with 750 million active users. The highly personal nature of Facebook data, as well as Facebook’s ability to influence diverse populations of web users, increases the significance of Facebook security mechanisms. In a recent study at the University of British Columbia, researchers used ‘socialbots’, or computer programs that imitate real Facebook profiles to gather vast quantities of personal data. The fake UBC accounts managed to steal 250GB of personal and marketable information from three thousand users by sending friend requests randomly.
One immediate conclusion of the study is that Facebook’s fraud detection can be exploited. Automated rate-limiting posts and friend requests enabled socialbots to bypass the website authentication system, potentially leaving the entire site open to abuse. Thus, the countless number of email and home addresses stolen from the UBC study suggests the possibility of large-scale malicious attacks and phishing scams. Note that IP addresses from accredited universities like Cornell would make it difficult for Facebook engineers to effectively differentiate real and illegitimate profiles. Moreover, with an understanding of online user behavior (ie. the more friendships people had on Facebook, the more likely they were to accept a ‘fake’ friend; some users are influenced by the purchases of their friends), Facebook can be manipulated as a tool of advertising or viral campaigns.
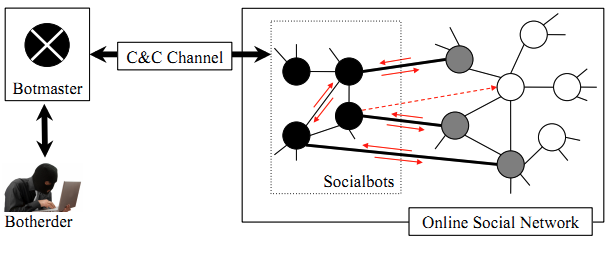
Until taking Networks, I related every computer problem to viruses destroying my computer software. Then I realized how we could apply some basic network concepts to explain a phenomenon described above. If I consider facebook users as nodes, then there are many paths connecting my friends and me. If I add this socialbot (from the experiment done by UBC researchers) just because it has a profile photo, there is a high chance that my friend with a strong tie will accept the request from this socialbot as well. This is an example of triadic closure property. For instance, according to the article, after randomly adding a person on facebook (20% success rate), a socialbot had a 60% success rate adding that person’s 2nd-degree friends. This could be explained a little better with the following diagram:
Researchers Flood Facebook With Bots, Collect 250GB Of User Data
After adding both my friends and me, socialbots would steal private information shared among us, which would then be transferred through the C&C channel to Botmaster and Botherder.
We could also explain the reason why the second-degree friends would add the socialbots using another concept from the class: information cascade. According to one definition of information cascade, decision making in a network is directly or indirectly influenced by other nodes within the network. Such influences could be from observing others or following decisions made by others. Thus, those of us benefiting from following friends (in terms of similarity of choices) tend to accept friend requests when seeing mutual friendships. After reading this article, I realized that I should refrain myself from accepting requests just by looking at mutual friends. We should all think about this issue. We may think that is it not a big deal to add any people without realizing how our everyday conversation could be tracked down by a third person.
The study done by UBC researchers is interesting because online social networks require us to engage in security challenges from programming and user points of views. The widespread use of Facebook makes it useful for further investigations of network phenomena.
Sources:
University of British Columbia (2011, November 1). Researchers Flood Facebook with Bots, Collect 250GB of User Data. TechCrunch. Retrieved November 2, 2011, from http://techcrunch.com/2011/11/01/researchers-flood-facebook-with-bots-collect-250gb-of-user-data/