The Power of Social Networks in Prisons
On campus, I am involved with Prisoner Express, a distance learning education program for incarcerated individuals. Prisoner Express provides an opportunity for self-expression and growth through newsletters and various programmings. I have had the wonderful opportunity of interacting and getting to read the creative pieces of incarcerated individuals and leave a positive impact on their lives. As I gained a deeper understanding on the topics in networks and how different entities are connected and interact with each other, I was interested in seeing how these topics could connect with a group of individuals that are often isolated from the rest of society.
Weak Ties: Something especially unique about Prisoner Express, its prisoners, and staff is that the program is built on the framework of weak ties. Weak ties are the connections between individuals that are not as close or intimate. All of the participants within Prisoner Express’ writing, theme, journal, and art programs are all connected by weak ties as their only form of communication is through the mail and not frequent. In the context of Prisoner Express, the incarcerated individuals participating in the program are often in a state of isolation, both physically and socially. By introducing weak ties, we can explore how even distant connections through newsletters, messages, or shared interests can contribute to a more diverse and supportive network for these individuals. The weak ties formed through Prisoner Express serve as bridges to new opportunities, resources, and a platform for self-expression that aren’t available within their immediate surroundings.
Network Exchange: The concept of network exchange becomes pertinent when considering the interactions within the Prisoner Express community. Exchanges occur as individuals share information, resources, and support. Within the physical confines of prison, opportunities for such exchanges are limited. However, through the Prisoner Express program, a unique network exchange takes place. The sharing of creative pieces, thoughts, and experiences becomes a form of currency, creating a valuable network where individuals exchange not only educational materials but also emotional connections. In this exchange, incarcerated individuals contribute their unique perspectives, stories, and talents, enriching the broader network with diverse experiences. Simultaneously, volunteers and participants from outside the prison system offer encouragement, feedback, and a sense of connection.
Network Effect: The network effect is also embodied in the operations of Prisoner Express. As more incarcerated individuals join Prisoner Express, the collective pool of knowledge, creativity, and shared experiences grows. This not only enhances the educational opportunities available to participants but also creates a supportive network where the value of interactions increases with each new contribution. The network effect emphasizes the positive feedback loop that occurs when more individuals connect and share within the program, leading to a richer and more vibrant community. The network effect extends beyond the confines of the prison system. As the network of volunteers and staff expands, so does the potential for societal impact. The collective influence of shared stories, perspectives, and educational resources has the capacity to raise awareness, challenge stereotypes, and contribute to a broader dialogue about the experiences of incarcerated individuals.
Real Life Telephone!
When I was younger, I would play a game called Telephone. The game’s goal was to receive messages and pass them around without any changes to the message’s meaning or phrasing. Very rarely, when I played the game with my classmates, would we accomplish the goal. Telephone mimics our world with social media, as information is not always consumed and given properly.
Social media is relatively new due to the advancement of technology. It has increased networks worldwide, as people have found ways to build relationships with people they don’t see regularly. It’s also allowed for information to travel faster, which is beneficial in times of crisis. Although it has benefits, it negatively impacts the dynamic of information cascades when people choose to be distrustful and ignorant, intentionally or not. Their actions overall lead to misinformation and the deterioration of connections. Information cascades can be labeled as people making choices based on observing people. With social media, people are less obligated to be truthful because often there are no consequences for them. Unfortunately, there are long-term consequences as concepts lose value.
During social justice movements, there have been times when a part of their campaign would lose value due to misinformation. During Black Lives Matter, there was a period when people were told to post Black squares in support of the movement. This was known as Black Out Tuesday. Leaders of the movement did not promote this, and it is not certain who started this idea. However, the information spread widely and did more harm than good, as many people participated in it. Information needed to educate people was being covered by posts that shared no information. Unfortunately, things like this happen often.
Although we can not stop the spread of misinformation completely, we should take steps to do so. I have noticed many apps taking action on this issue. Apps such as X have been taking steps by labeling possible posts as possibly false before people consume and share them. We should also hold ourselves accountable for the information we consume and fact-check because not everything shared is true.
https://help.twitter.com/en/resources/addressing-misleading-info
https://www.wikihow.com/Play-the-Telephone-Game
LinkedIn: A Real World Example of Strong and Weak Ties and Strong Triadic Closure
LinkedIn’s platform is a complex professional and social network that exemplifies class network theories related to the concepts of strong and weak ties. These connections foster professional development and networking success on the platform, offering advantages to users and exemplifying the ideas of strong triadic closure and the strength in strong and weak ties.
Strong connections on LinkedIn, often close family members, friends, or long-term colleagues, hold significance for several reasons. Firstly, these connections are built on a foundation of trust and mutual support, making them valuable for job recommendations and references. Such endorsements from close contacts carry substantial weight with potential employers. Additionally, strong ties facilitate in-depth exchanges of industry insights and professional advice. This rich knowledge sharing can be instrumental in overcoming career challenges and making well-informed decisions. Although strong ties are advantageous in their ability to provide support in career development, Gradovetter asserts that strong ties do not offer novel information or new opportunities for users in a network. This same theory also applies to LinkedIn.
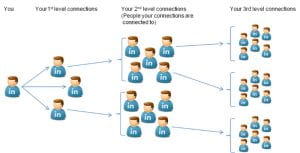
Weak connections on LinkedIn, which may include friends of friends, acquaintances or professionals met in passing. Weak ties serve as bridges between diverse professional groups, offering access to new information and opportunities that strong ties may not provide, as they often circulate within similar circles. These connections bring fresh perspectives and knowledge from diverse industries or geographical locations, enriching one’s understanding of different business opportunities and engagements. LinkedIn’s structure of showing 1st, 2nd, and 3rd level connections actively promotes the formation of weak ties. Users are more inclined to connect with 2nd and 3rd level connections as they observe their interactions and engagements with mutual connections, enhancing the likelihood of discovering new opportunities and expanding their professional networks. The exposure to 2nd and 3rd level connection content confirms LinkedIn’s correlation with strong triadic closure as shared 1st level connections between two users often lead to the creation of a connection between the two users. The principle of strong triadic closure underscores that strong connections often grant access to otherwise exclusive networks. When two individuals share a mutual strong connection, they are more likely to form a strong tie themselves, thereby expanding each other’s networks.
The interplay between strong and weak ties on LinkedIn is further highlighted by the platform’s design. Users are exposed to the activities of their connections, including likes, comments, and shares. This feature not only reinforces existing ties by keeping users informed about their connections’ professional activities but also encourages the formation of new ties. Witnessing a 1st level connection interact with someone else can lead to a 2nd or 3rd level connection, effectively building a bridge to a new network. Over time, these new connections can evolve, potentially becoming strong ties through continued interaction and shared professional experiences. This platform structure also offers the potential to share novel information and opportunities to 2nd and 3rd connections, allowing for greater exposure to potential job opportunities and industries that may have remained unexplored otherwise.
More so, LinkedIn advances the value of weak ties as users are motivated to create a large network of connections to get to over 500 total connections on the platform. This feature further motivates users to connect with connections of connections, thus propelling the strong triadic closure theory. The more connections one has leads to a greater amount of information accessed as users continue to see content of their connection’s connections while increasing their network.
Thus, LinkedIn serves as a network where the principles of strong and weak ties, as well as strong triadic closure, come to life in real-time. Strong ties offer depth, trust, and knowledge exchange, while weak ties provide breadth, diversity, and access to fresh opportunities. The platform’s ability to showcase various levels of connections (1st, 2nd, and 3rd) and the interactivity among them further solidifies its role as a powerful tool for professional networking and career development. Understanding and leveraging both types of connections can lead to a more robust and dynamic professional network, which is essential for career advancement in today’s highly technological world.
Weak Ties in college
As students or faculties of Cornell University, we all live in our own small society.
Even though you might have not met everyone on campus, the identity of being a Cornell student creates automatic weak ties between students and faculties and these weak ties become the alumni networks.
These ties between students develop based on common identity rather than a direct emotional or social connection.
It is interesting to look into how connections are present even in the absence of contact as long as there is a sense of belonging.
Public Goods Provision: The Role of Wealth Redistribution and Multiple Public Goods
We left off class at public goods, so I thought that I would do a blog post about this paper I found about public goods. Building upon previous research, this study investigates the intricate relationship between contributions, wealth redistribution, and equilibrium outcomes. I tried my best to summarize what I got from reading the article.
Strong and Weak ties in Social Networks
As we talked about strong and weak ties in class, it reminded me of a different course I took, Comms 2450. In this class we talked about how strong and weak ties can give different opportunities. Weak ties can provide you with more information outside your small group of friends like job opportunities, while strong ties can provide you with more support like large favors. This reminded me of how social media is set up. User’s network consists of strong and weak ties which gives users feeds that consist of people they interact with more, strong ties. Although these accounts may not be strong ties in real life, in the user’s social media network they are. With social media, users can connect to anyone in the world and can create a strong, long-lasting friendship. Weak ties are also very important and relevant in social media. Many people on Instagram, Facebook, or X have hundreds of friends/connections and a vast majority of them are weak ties. This allows users to see posts from a diverse group of opinions unlike in person someone might only be around people with the same ideals as them. Social networks online allow political movements to grow exponentially because of weak ties. Strong and weak ties are everywhere and are very important to social networks.
I also wanted to include that I recently talked to one of my friends’ parents who has his own digital network. He apparently has all the contact information of all his friends or people he has met on his computer. He says he has had it since he was 20 although back then it was on paper. This interested me because we learned about the strong triadic closure theorem and I wanted to see if his network held it. Since his network consists of a lot of friends of friends, I think it will hold even though the strong triadic closure doesn’t always pertain to real life. Even though I haven’t been able to confirm my hypothesis, I found it very interesting and want to start my own. Without this class, I would have never thought that a personal social network would have been interesting and I am so happy I took this course.
Structural Balance Theorem and Rival Schools
We can observe two rival schools, Cornell and Harvard. We can also easily observe that students at Cornell are all on good terms with each other, and likewise for Harvard students. Thus, we can group students in Cornell into one group, and students in Harvard into another group. As these schools are rivals, we can observe the relationships between Cornell students and Harvard students as enemies.
At a low level, we can observe the Structural Balance Property, which states: for every set of three nodes, if we consider the three edges connecting them, either all three of these edges are labeled +, or exactly one is labeled +, otherwise is imbalanced. We can observe four possible set of three nodes: (Harvard, Harvard, Harvard), (Cornell, Cornell, Cornell), (Harvard, Harvard, Cornell), and (Cornell, Cornell, Harvard). The set of (Harvard, Harvard, Harvard) nodes are all connected by positive edges. The set of (Cornell, Cornell, Cornell) nodes are all connected by positive edges. The set of (Harvard, Harvard, Cornell) is connected with two negative edges from Cornell to each Harvard node, and a positive edge between the Harvard nodes. The set of (Cornell, Cornell, Harvard) is connected with two negative edges from Harvard to each Cornell node, and a positive edge between the Cornell nodes. Thus, we see that these sets all satisfy the Structural Balance Theorem.
Furthermore, we can see that this property implies the global property of the Balance Theorem.
We can apply the Balance Theorem to this situation. We know the Balance Theorem to be: If a labeled complete graph is balanced, then either all pairs of nodes are friends, or else the nodes can be divided into two groups, X and Y, such that every pair of nodes in X like each other, every pair of nodes in Y like each other and everyone in X is the enemy of everyone in Y. In our scenario, we see the complete graph as all students in Cornell and Harvard connected by edges. Nodes can be connected into pairs of (Cornell, Harvard), (Harvard, Harvard), or (Cornell, Cornell). We can see a (Cornell, Harvard) pair is connected by a negative edge. We can see (Harvard, Harvard) and (Cornell, Cornell) pairs is connected by a positive edge. We can easily observe all students from Cornell represented by nodes and connected by positive edges, and all students from Harvard represented by node and connected by positive edges. Additionally, we observe that the nodes of students from Harvard are all connected to the nodes of students from Cornell by negative edges. Thus, we can observe the Balance Theorem.
The Job Market as an Auction
As a Cornellian, the subject of jobs and internships never seems too far away from the mind’s eye. Here’s a fun thought experiment about the job market and how it can be viewed as an auction. For starters, let’s establish the bidders and sellers. From the perspective of a student, it seems only natural to view job openings as the items being sold and job applicants as the bidders of each item. A winning bidder gets a job and the other unsuccessful bidders must continue bidding on other jobs. To simplify things, suppose there is one item being sold (one job opening) and multiple bidders (multiple applicants). In a regular auction, the winning bidder pays for the item with money. While it may seem counterintuitive at first, this payment method also holds in our job market analogy. A successful job applicant, who wins the bid, pays for the job with the amount of profit he brings to the company after he starts working there. A candidate’s true value is the amount of profit he can actually bring to the company, if hired. This true value is correlated with his knowledge, skills, experience, etc. The amount of profit each candidate claims to bring to the company, if hired, is his bid. During the auction, each job applicant will make a bid, and the job applicant with the highest bid will receive the job.
Given this setup, we can ask if it is a dominant strategy to bid truthfully. In other words, is it the best response of every job applicant to be honest in the amount of profit they can bring to the company, if hired. To see if bidding truthfully is a dominant strategy, suppose everyone bids truthfully. Then, the most qualified candidate will end up bidding the highest value and subsequently will be the one to receive the job offer. Now suppose one of the other candidates, who is less qualified for the job, bids untruthfully by bidding higher than his true value. This can be done through pretending to have work experience he does not have or by exaggerating his skillset. If the untruthful bidder ends up bidding a value higher than the most qualified candidate’s true value, then the untruthful bidder gets the job. As such, truthful bidding is not a dominant strategy.
There are some obvious limitations to the scenario presented above. For example, job applicants will likely have background checks, take technical interviews, and go through other screening processes to ensure that their bid is in fact their true value. If a candidate is found guilty of untruthful bidding, they will be taken out of the applicant pool for that job. However, in the real world, it is clear that this is not always guaranteed to happen, given the amount of people who have overexaggerated their resumes and still landed job offers. Thus we could go one step further in our bidding analogy and say that job applicants will take into account the risk of being found out when they decide to bid untruthfully. Intuitively, the more untruthful the bid (the more the applicant stretches the truth or lies about his abilities), the easier it is to discover the bid was in fact untruthful. We could calculate the expected value of the job applicant when he stretches the truth versus when he outright lies on his resume. If given the right data, these expected values could be calculated, giving more interesting factors to consider in this thought experiment.
Thoughts on the Urn Model
In the course, I found many topics particularly interesting. The one I like the best is the urn model. I am curious about its broader applications in real life, as it seems to be a useful tool for modeling information cascades and applying Bayesian principles. Additionally, it bears a resemblance to statistical procedures involving drawing data with replacement, such as bagging in machine learning.
I find the urn model intriguing, especially in scenarios where individuals make decisions based on information from others. When a student has information from multiple sources, they tend to follow what others are saying. In contrast, when they have only one previous person’s guess and their own draw, they are more likely to choose based on their own observation. This phenomenon resembles an information cascade. Interestingly, this concept also resonates with business development strategies. For instance, businesses can leverage the urn model in queueing systems to simulate customer arrivals and service requests. When customers observe a long waiting queue, they interpret it as a positive signal about the business’s popularity. There have been instances where new stores hire individuals to stand in line, creating a commercial effect and attracting customers.
Another relevant application I discovered is in machine learning, specifically in Bagging (Bootstrap Aggregating). This technique involves training multiple models on different subsets of the training data. The process is analogous to drawing samples with replacement from an urn. However, it’s important to note that if the subsets are too similar or contain repetitive data (similar to the case where many students hear the same information), it can lead to an information cascade effect— the model can result in a low training accuracy. This parallel between the urn model and machine learning practices underscores the versatility and applicability of these probabilistic concepts across various domains.
To conclude, these are only some thoughts that occurred to me throughout the class and they can be problematic. However, my favorite part of this class is that we get to integrate scientific models into social and economic settings. It encourages me to find the usefulness and application of what I learn!
Network Theory in Financial Markets – A New Frontier in Understanding Market Dynamics and Risk Assessment
In the intricate world of financial markets, the application of network theory offers a transformative approach to understanding market dynamics and assessing systemic risks. Traditional models, often used by regulators and policymakers, have shown limitations, especially evident during the 2007-2008 financial crisis. These models typically view financial systems as collections of isolated actors or as a homogenous mixture where each actor interacts equally with all others. However, the crisis starkly revealed the inadequacy of such models in capturing the highly heterogeneous and interconnected nature of financial systems.
Network theory steps in to fill this gap. It highlights the crucial interplay between the structure of financial networks, the heterogeneity of financial actors, and the dynamics of risk propagation, especially contagion. Contagion in financial markets can be likened to a domino effect, where the instability of certain institutions reverberates throughout the entire system. This systemic risk is a product of the collective network, bearing similarities to collective phenomena in physics.
A key aspect of network theory in finance is understanding how individual banks, perceiving the riskiness of their direct connections, may underestimate the collective default risk heightened by interconnected loans. The complexity lies in the confidentiality of loan agreements, necessitating innovative techniques to infer key properties of interbank networks from partial information.
The use of network theory in financial markets has gone beyond theoretical frameworks to practical applications. Researchers have developed methods to reconstruct financial networks, providing tools for central banks to conduct more reliable stress tests on financial systems. These methods have shown their effectiveness, with some studies indicating that a network analysis, accounting for the observed heterogeneity of banks, could have predicted the 2007-2008 crisis years in advance.
The evolution of financial network theory has led to a wider recognition of its importance in monitoring financial stability and informing macroprudential regulation. Policymakers and researchers now commonly agree that a network perspective is essential in studying and managing systemic risk. This shift in perspective is also evident in the policy actions and discourses of the highest financial authorities in both the US and the EU.
As financial markets continue to evolve and interconnect, the role of network theory in understanding and managing financial risks becomes increasingly significant. It provides a foundational science for financial risk managers, macro-economic planners, and regulators to gauge potential future downturns and design strategies to mitigate these risks effectively.
The exploration of network theory in financial markets marks a significant advancement in how we comprehend and navigate the complex, interconnected nature of today’s financial world. It stands as a testament to the interdisciplinary nature of modern finance, where concepts from physics and mathematics converge with economics and finance to forge new pathways in understanding and managing financial risks.
References:
– “When physics meets financial networks” on Phys.org. [Phys.org](https://phys.org/news/2021-06-physics-financial-networks.html)
– “Using Network Theory to Understand the Interconnectivity of Financial Risk” on Moody’s RMS. [RMS](https://www.rms.com)
– “The physics of financial networks” in Nature Reviews Physics. [Nature Reviews Physics](https://www.nature.com/articles/s42254-021-00322-5)
« go back — keep looking »