Finding Pressure Points in Modern Crime Networks
For hundreds of years there have been various forms of crime rings around the globe. However, with the advancement of modern technology, crime rings are becoming more and more complex. Researchers in the National Science Foundation analyzed the question, “What does organized crime really mean in cyberspace?” Through their research the group used Klout’s Ranking System. This system assigns a number between one and one hundred that represents how much influence the assigned individual has. (One being minimal influence and one hundred being extremely influential) For example, according to the Klout Score official website, President Barack Obama has a Klout Score of 99. This score is calculated by analyzing how many connections the individual has in the given network, which could be very similar to some of the networks we have discussed in class.
The research team hypothesized the Klout system could not only be used to find influential people in the public scene, but also to find influential members in high-level cyber crime areas. According to Britt Faulstick, the author of Researchers Understand Organized Cybercrime, “more connected cybercriminals hold a great deal of power… because they are able to interact directly with a number of other members without going through an intermediary.” Similar to the idea of strong and weak ties, cybercriminals must be able to identify their stronger ties in order to maintain security from the authorities. If the ties are too weak, one of the links could lead to an individual that could get the cyber criminal in trouble with the law.
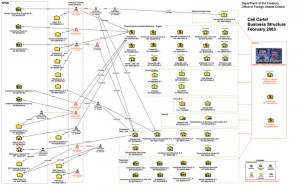
In 2003, the U.S. Department of the Treasury identified the below network. This tree illustrates the leadership dynamics of the Cali drug cartel. Through analyzing communications, authorities are able to pinpoint who is in charge of the cartel. The idea of being connected comes into play in this graph too as the entire graph is connected and the layout seems to form a hierarchy tree of the members of the cartel.
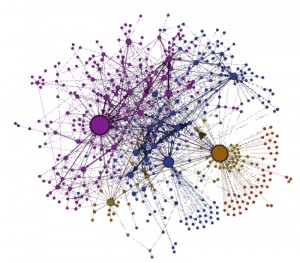
In another study, conducted by researchers at Drexel’s Privacy, Security and Automation Lab, a social network illustrating the “cybercrime forum called Carders,” shown below, was created to look at the different ‘gangs’ that were formed online. The study found that there were a small number of essential individuals that were central to communication on the cybercrime forum. These select individuals formed clusters of communication links around them with minimal communication with other clusters. However, the network is still likely connected, as the ‘ringleaders’ do seem to have connections. Drexel’s Lab also suggests that the reason for this distribution of tight niched gangs has to do with the overall layout of the cartels and cybercrime rings. The lab thought that these different groups corresponded to different responsibilities within the group; for example, Carders “mainly discussed drugs” while another group mainly handled stolen electronics, which could be the reason the tightly niched grouping.
Faulstick also discusses the meaning of the Dunbar Number, which is significant because the value identifies the theoretical maximum number of trusted connections one individual can have. According to Forbes this number lies around 150. However, in organized crime it is sometimes necessary to increase this number in an effort to expand business. So, how does a cybercrime group go about increasing its maximum number of ‘strong ties’? Drexel believes that in order to increase Dunbar’s number the group would need “a broad distribution of leadership,” which can also be seen by the hierarchical graphs above.
Modern crime networks are becoming more complex as society becomes more technologically focused, and how to catch cybercriminals is a continuously changing process. Yet, using some graph theory and network illustration, similar examples in our class, law enforcement seems to be hot on the trails of a wide variety of criminals.
Sources:
http://drexel.edu/now/archive/2015/April/organized-cybercrime/
http://www.forbes.com/sites/tjmccue/2013/01/15/social-media-maximum-150-friends/